Hey There,
I am wondering if anyone knows the best way to process bearer token authentication?
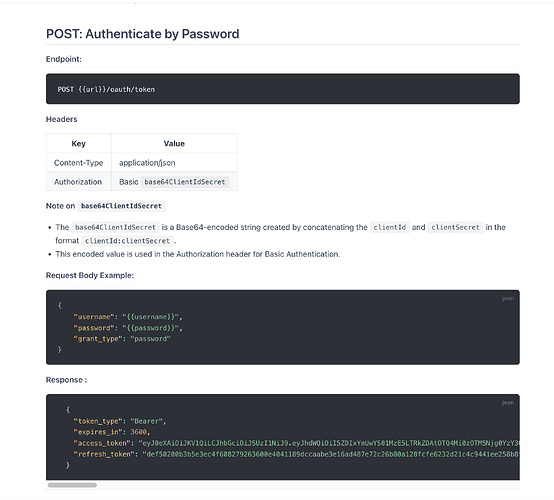
Effectively I need to:
POST {{url}}/oauth/token
with header authentication and body user/pass/type, then it returns a bearer token (example).
{
"token_type": "Bearer",
"expires_in": 3600,
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJhdWQiOiI5ZDIxYmUwYS01MzE5LTRkZDAtOTQ4Mi0zOTM5Njg0YzY3ODIiLCJqdGkiOiIyMTE0MTFlYWExZGU1YTRlNzcxOGRmODk1N2M2YWQyNzAzZTk0YzBhMjJjNDZlNTM4NWZmMTM0N2FjNDhiYzFkNjRlOTU2ODE0OWZjZmQ3NiIsImlhdCI6MTcyNzc1OTEzOS44MzI2NjEsIm5iZiI6MTcyNzc1OTEzOS44MzI2NjQsImV4cCI6MTcyNzc2MjczOS44MDQwMDYsInN1YiI6IjEiLCJzY29wZXMiOltdfQ.YTbSjKgZg4v8D2n11Az9TqjiJVvTyQPl-8BoqqkdfGhUlkMZ4DZ-JT49m7KPh-Y6slX8qzr_ZMryeKhbN_avR0lRxRt-xPkuXUbvGld-TpWHbsJ6eR7QK2UGyzMhM_CRQQH9MYNx8tIcNTON_mmp6DcqV9GcHzP20rUfkUIByvwaZF36l1rx3RosRjttvG1Jff9SeFcaHAwpy8uk9iu0nplOS-Se88Se8Ir8TU_kEZfUudwPw-7GEsQ2Bz9Z_AuZheVvBt8uPjlCGGjfGl7dcG_wy4JYkb3fyKe8IqTcTb6vsjC24pvtijkjaJljUaePzaPp5k5EdGXxLtYkAhxDBSmaxSicVesh-EHbqJHQmwc_CPN9K6tiuSv6YmGEfau4Mn6ryULDyjngvvN_gvAj7-F2cwk76pZWfcVMPazG40CfSyrfWG8xv7kuYNiZLQ48k8oahDdqoYK9a0MhBXmdq4AO6OKKPhp9_rS86ecB1vWNqKOJg3pnDq9cgsR26vXADrpJiL4ETDl3djR4sBGpBaqUstSC79H91yGApxfOvUWVxyA7ou_dEoryMaW6iVzwEv5-hZG9c3CoNEupvd_YeFjFSby-eBQ8AjubZm_B_NUbcJq7G4XoV2K1Gzpvfcvywb9F5cFANX-aoBLESauW8kPi7MA3n2QrXpadtmgBSD4",
"refresh_token": "def50200b3b5e3ec4f608279263600e4041189dccaabe3e16ad487e72c26b80a128fcfe6232d21c4c9441ee258b8f03964f4685643865677e2e2613a7ed7251849f13934028f84dc33cbf589a6ce0c37e98066e561fbe16997751a831dd9df294a690c3ac43beab27cb86e64fa7eb1fe572c514fb5487d929dfc6b415f34803ce7168cd468fbc9a0f30b460244a8b9da559ec5dfe1b7b01f52219150e02d75a001007fed26a1fd66f2086fed15e4961f9481fdbdac032b3c055e5d6509e615e831fa6b395195cc561b14be95d9f16bf73a77bedcf20b9348e11d1a2a8bab3abaa62f585f1aa804e53b7f8e297b295a18b146eea8ada82ee4ea8d4e6cfdd563f1f06947b5b84ad1e02551674d302a77d1f0949f10324e37ed7c55620c0271a871555784b3d256ca7a48d261ca7afcac50235ae75066a73b7dd99034549a0c9cefb98685527f32b05f13cb681432919644766bc56fb1ad3412c43e96037cd1511d175460ee6f0d5e12a7e2ab90b2ae6e12be2e1a1f62f40ffe80457cd96f850adb5e3c4d23"
}
I need the access_token for subsequent calls, and then can recall the api once it has expired to get new access_token (either via refresh_token or user/pass").
I feel like it is a custom auth, like this:
{
"headers": {
"Authorization": "Basic {{bearer}}",
"Content-Type": "application/json"
},
"body": {
"username" : "",
"password" : "",
"grant_type": "password"
}
}
but not sure where the access_token get stored or how its knows the access_token is active.
Cheers
Chris