How to consume Okta events came up in a support conversation recently, and it seemed to me the general approach is worth sharing.
A quick look at Event hooks concepts | Okta Developer suggests Okta supports webhooks and will send two types of requests:
- a one-time
GETrequest is used for verifying your endpoint -
POSTrequests are used for the ongoing delivery of events
On the n8n side of things, this means we need two separate Webhook nodes using the same path but different HTTP methods (GET and POST). The GET webhook has to respond with a special JSON object required by Okta, so we’ll also need a Respond to Webhook node connected to it.
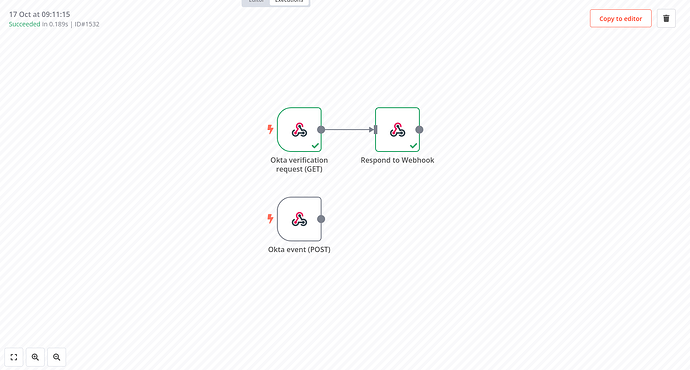
Here’s how this looks in a workflow:
When implementing this I suggest you activate your workflow immediately and exclusively work with the Production URL from your webhook nodes. Otherwise you will have to go through the registration process with Okta twice (first time for the test URL, then another time for the production URL).
With the workflow in place and activated, head to Workflows → Event Hooks on your Okta dashboard. and click Create Event Hook. Fill in your production URL and pick the events you want to subscribe to. Click Save & Continue, then Verify. Okta will now send a request to your GET webhook. Provided you have everything set up properly you should now see the first execution in the n8n execution history:
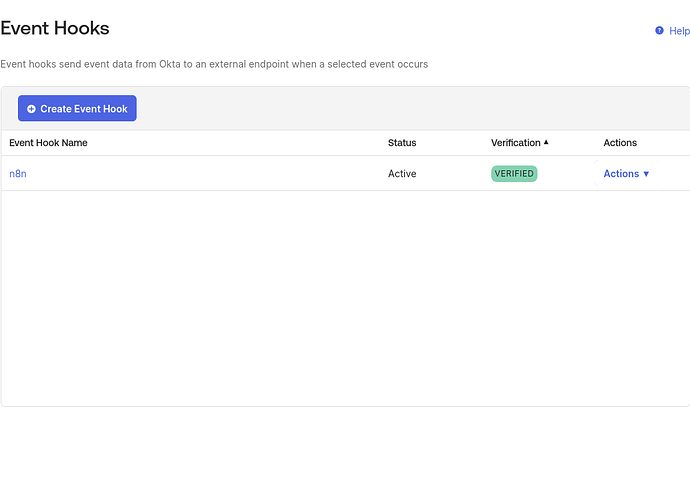
Okta will now also show your webhook as “active” and “verified”:
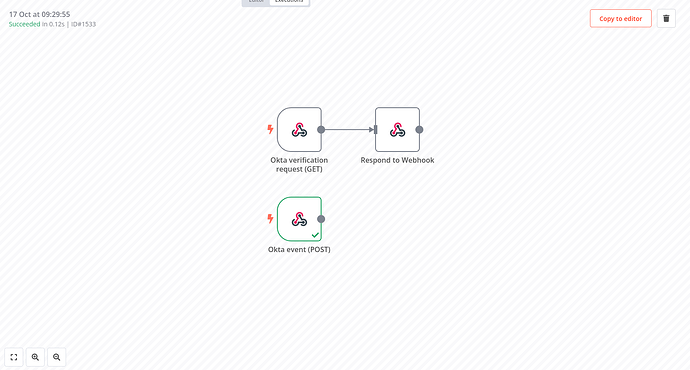
Future Okta events will now trigger the POST webhook in n8n. You can also use the data received from Okta in the workflow editor by clicking the Copy to editor button shown in the upper right:
The information provided by Okta is rather comprehensive, so chances are you won’t have to call their API separately to fetch more details.
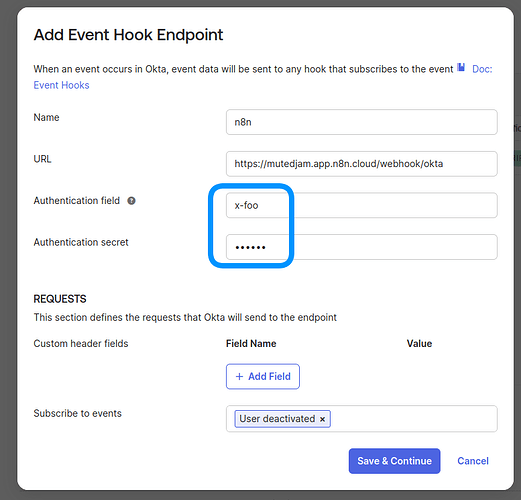
To further harden your setup you want to add headers to the webhooks sent by Okta. To do so, fill out Authentication field and Authentication secret in your Okta event hook configuration:
In n8n you can then configure Header authentication on your webhook to reject unauthenticated requests: