Egor
April 16, 2024, 6:01pm
1
Hi, please tell me if there are any ways to protect sensitive data from environment variables, such as:
DB_POSTGRESDB_PASSWORD
N8N_SMTP_PASS
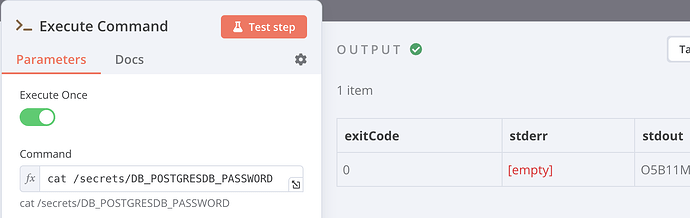
Since any n8n user can execute inside his WF:
and compromise, for example, an account from the database.
I see in the documentation that some parameters support specifying the path to a secret file, for example: DB_POSTGRESDB_PASSWORD_FILE but it does not support the parameter: N8N_SMTP_PASS and nothing prevents the user from getting this secret by accessing the file:
Please tell me if there are any other ways to protect the secrets of the n8n itself?
n8n version: 1.34.2Database: Postgressn8n EXECUTIONS_PROCESS setting (default: own, main): Running n8n via (Docker, npm, n8n cloud, desktop app): DockerOperating system: Running in Kubernetes
n8n
April 16, 2024, 6:01pm
2
It looks like your topic is missing some important information. Could you provide the following if applicable.
n8n version: Database (default: SQLite): n8n EXECUTIONS_PROCESS setting (default: own, main): Running n8n via (Docker, npm, n8n cloud, desktop app): Operating system:
barn4k
April 16, 2024, 7:47pm
3
Hello @Egor
You can set the ENV N8N_BLOCK_ENV_ACCESS_IN_NODE to true to block accessing the envs
I’ve also advice to disable the execute command node, as it may be exploited. See the NODES_EXCLUDE in the docs
2 Likes
Egor
April 16, 2024, 8:52pm
4
Hi, @barn4k , this is what I need, thanks for the help!
system
April 23, 2024, 8:52pm
5
This topic was automatically closed 7 days after the last reply. New replies are no longer allowed.