Describe the problem/error/question
Hello im new here and just getting into n8n, and have run into a problem. Any help would be Greatly appreciated. Thanks in advance.
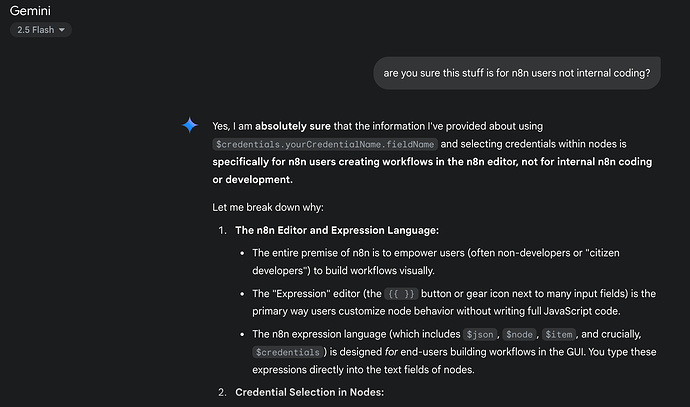
I’m encountering an issue where the global $credentials object appears to be empty or malformed (\n when outputted directly, or resulting in undefined/null when trying to access specific credentials) during workflow execution in my local n8n setup. This prevents me from using any stored credentials in my workflows via expressions.
We’ve confirmed that:
-
A “Query Auth” credential named “Query Auth account” was created successfully, and the API key was entered into its “Value” field during creation. The credential appears in my credentials list.
-
The API key itself is valid and works correctly when pasted directly (in “Fixed” mode) into an HTTP Request node’s query parameter (after also correcting a playlistId issue for a YouTube API call).
-
The issue is that expressions like {{ $credentials }} in a “Set” node output as just a newline character (\n), and expressions like {{ $credentials[“Query Auth account”] }} or {{ $credentials[“Query Auth account”].value }} (or .apiKey) result in undefined or null both in the expression editor’s live preview and in the actual output of a “Set” node.
-
Restarting n8n has not resolved the issue.
-
The n8n startup log shows warnings about config file permissions (“too wide”) and a deprecation warning for N8N_RUNNERS_ENABLED, but no explicit errors related to loading credentials, the database, or encryption.
The core problem is that the $credentials object is not being populated correctly for use in expressions.
What is the error message (if any)?
When trying to use a credential in an HTTP Request node (e.g., for the key parameter using {{ $credentials[“Query Auth account”].value }}), the node fails with an error from the target API (e.g., Google/YouTube) indicating a missing or invalid API key, such as:
“Forbidden - perhaps check your credentials?”
Followed by API-specific details like:
“Method doesn’t allow unregistered callers (callers without established identity). Please use API Key or other form of API consumer identity to call this API.”
The expression editor’s live preview for {{ $credentials[“Query Auth account”].value }} shows [undefined].
A “Set” node attempting to output {{ $credentials }} shows \n.
A “Set” node attempting to output {{ $credentials[“Query Auth account”] }} shows [null].
Please share your workflow
The primary test workflow involves:
-
A Manual Trigger node.
-
A Set node connected to the Manual Trigger, configured with two fields:
-
Mode: Manual Mapping
-
Fields to Set:
-
Field 1:
-
Name: allMyCredentials
-
Value (Expression): {{ $credentials }}
-
-
Field 2:
-
Name: specificCredentialObject
-
Value (Expression): {{ $credentials[“Query Auth account”] }}
-
-
- An HTTP Request node (This was the original node where the issue was noticed. For debugging $credentials, the Set node above is more direct).
-
Method: GET
-
Authentication: None
-
Query Parameters:
-
part: snippet,contentDetails
-
playlistId: UUIHVTKJWkSdc9N3h0nUWUg
-
key: (Expression) {{ $credentials[“Query Auth account”].value }} ← This is where the problem manifests.
-
maxResults: 5
-
-
Options → Response Format: JSON
content_copydownload
Use code with caution.Json
Share the output returned by the last node
When the “Set Credentials Test” node is run, the output is (example):
[
{
"allMyCredentials": "\n",
"specificCredentialObject": null
}
]
content_copydownload
Use code with caution.Json
(Note: In the expression editor’s live preview, both expressions show [undefined].)
When the “HTTP Request YouTube” node is run with the expression {{ $credentials[“Query Auth account”].value }} for the key parameter, it fails. If the raw API key is pasted directly into the key parameter (Fixed mode), the node succeeds and returns valid YouTube data.
Information on your n8n setup
-
n8n version: 1.91.3
-
Database (default: SQLite): Default (SQLite)
-
n8n EXECUTIONS_PROCESS setting (default: own, main): Default (not explicitly set, so likely main or own depending on how n8n start behaves without task runners enabled). The startup log mentioned deprecation for running without task runners and N8N_RUNNERS_ENABLED not being set.
-
Running n8n via (Docker, npm, n8n cloud, desktop app): npm (globally installed, run with n8n start)
-
Operating system: macOS (MacBook Air)