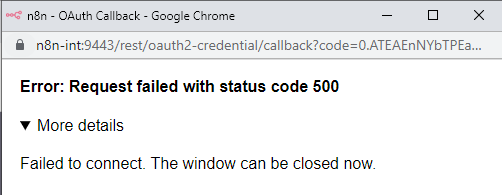
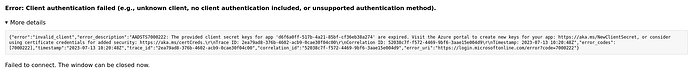
Hi @MutedJam
I did some more testing.
- Removing the N8N_USER_DEPRECATED_REQUEST_LIB setting does not change anything, I have the same behaviour with and without the setting. This also means that proxy support seems to be there (although unclear whether it is working).
- I did some tests on my local installation that does not require the use of a proxy. This setup works as expected. The only difference remaining seems the proxy stuff.
When working on my setup, I am using a free outlook.com account. The other setup is using a Azure AD integrated account. Maybe this makes some difference. I have scheduled a meeting for tomorrow to test with another guy as I do not have access to the required AAD credentials myself.
The request to Microsoft on my installation looks like this:
n8n-n8n-1 | 2023-07-17T12:58:43.612Z follow-redirects options {
n8n-n8n-1 | maxRedirects: 21,
n8n-n8n-1 | maxBodyLength: 10485760,
n8n-n8n-1 | protocol: 'https:',
n8n-n8n-1 | path: '/common/oauth2/v2.0/token',
n8n-n8n-1 | method: 'POST',
n8n-n8n-1 | headers: {
n8n-n8n-1 | Accept: 'application/json, application/x-www-form-urlencoded',
n8n-n8n-1 | 'Content-Type': 'application/x-www-form-urlencoded',
n8n-n8n-1 | 'User-Agent': 'axios/0.21.4',
n8n-n8n-1 | 'Content-Length': 278
n8n-n8n-1 | },
n8n-n8n-1 | agent: undefined,
n8n-n8n-1 | agents: { http: undefined, https: undefined },
n8n-n8n-1 | auth: undefined,
n8n-n8n-1 | hostname: 'login.microsoftonline.com',
n8n-n8n-1 | port: null,
n8n-n8n-1 | nativeProtocols: {
n8n-n8n-1 | 'http:': {
n8n-n8n-1 | _connectionListener: [Function: connectionListener],
n8n-n8n-1 | METHODS: [Array],
n8n-n8n-1 | STATUS_CODES: [Object],
n8n-n8n-1 | Agent: [Function],
n8n-n8n-1 | ClientRequest: [Function: ClientRequest],
n8n-n8n-1 | IncomingMessage: [Function: IncomingMessage],
n8n-n8n-1 | OutgoingMessage: [Function: OutgoingMessage],
n8n-n8n-1 | Server: [Function: Server],
n8n-n8n-1 | ServerResponse: [Function: ServerResponse],
n8n-n8n-1 | createServer: [Function: createServer],
n8n-n8n-1 | validateHeaderName: [Function: __node_internal_],
n8n-n8n-1 | validateHeaderValue: [Function: __node_internal_],
n8n-n8n-1 | get: [Function: get],
n8n-n8n-1 | request: [Function: request],
n8n-n8n-1 | setMaxIdleHTTPParsers: [Function: setMaxIdleHTTPParsers],
n8n-n8n-1 | maxHeaderSize: [Getter],
n8n-n8n-1 | globalAgent: [Getter/Setter]
n8n-n8n-1 | },
n8n-n8n-1 | 'https:': {
n8n-n8n-1 | Agent: [Function: Agent],
n8n-n8n-1 | globalAgent: [Agent],
n8n-n8n-1 | Server: [Function: Server],
n8n-n8n-1 | createServer: [Function: createServer],
n8n-n8n-1 | get: [Function: get],
n8n-n8n-1 | request: [Function: request]
n8n-n8n-1 | }
n8n-n8n-1 | }
n8n-n8n-1 | }
The request on the proxied instance looks like this:
n8n-n8n-1 | 2023-07-17T13:49:59.363Z follow-redirects options {
n8n-n8n-1 | maxRedirects: 21,
n8n-n8n-1 | maxBodyLength: 10485760,
n8n-n8n-1 | protocol: 'http:',
n8n-n8n-1 | path: 'https://login.microsoftonline.com/common/oauth2/v2.0/token',
n8n-n8n-1 | method: 'POST',
n8n-n8n-1 | headers: {
n8n-n8n-1 | Accept: 'application/json, application/x-www-form-urlencoded',
n8n-n8n-1 | 'Content-Type': 'application/x-www-form-urlencoded',
n8n-n8n-1 | 'User-Agent': 'axios/0.21.4',
n8n-n8n-1 | 'Content-Length': 1134,
n8n-n8n-1 | host: 'login.microsoftonline.com',
n8n-n8n-1 | 'Proxy-Authorization': 'Basic xxxxxxxxxxx'
n8n-n8n-1 | },
n8n-n8n-1 | agent: undefined,
n8n-n8n-1 | agents: { http: undefined, https: undefined },
n8n-n8n-1 | auth: undefined,
n8n-n8n-1 | hostname: 'proxy.szh.loc',
n8n-n8n-1 | port: '8080',
n8n-n8n-1 | host: 'proxy.szh.loc',
n8n-n8n-1 | beforeRedirect: [Function: beforeRedirect],
n8n-n8n-1 | nativeProtocols: {
n8n-n8n-1 | 'http:': {
n8n-n8n-1 | _connectionListener: [Function: connectionListener],
n8n-n8n-1 | METHODS: [Array],
n8n-n8n-1 | STATUS_CODES: [Object],
n8n-n8n-1 | Agent: [Function],
n8n-n8n-1 | ClientRequest: [Function: ClientRequest],
n8n-n8n-1 | IncomingMessage: [Function: IncomingMessage],
n8n-n8n-1 | OutgoingMessage: [Function: OutgoingMessage],
n8n-n8n-1 | Server: [Function: Server],
n8n-n8n-1 | ServerResponse: [Function: ServerResponse],
n8n-n8n-1 | createServer: [Function: createServer],
n8n-n8n-1 | validateHeaderName: [Function: __node_internal_],
n8n-n8n-1 | validateHeaderValue: [Function: __node_internal_],
n8n-n8n-1 | get: [Function: get],
n8n-n8n-1 | request: [Function: request],
n8n-n8n-1 | setMaxIdleHTTPParsers: [Function: setMaxIdleHTTPParsers],
n8n-n8n-1 | maxHeaderSize: [Getter],
n8n-n8n-1 | globalAgent: [Getter/Setter]
n8n-n8n-1 | },
n8n-n8n-1 | 'https:': {
n8n-n8n-1 | Agent: [Function: Agent],
n8n-n8n-1 | globalAgent: [Agent],
n8n-n8n-1 | Server: [Function: Server],
n8n-n8n-1 | createServer: [Function: createServer],
n8n-n8n-1 | get: [Function: get],
n8n-n8n-1 | request: [Function: request]
n8n-n8n-1 | }
n8n-n8n-1 | }
n8n-n8n-1 | }
Not perfectly equal, but I guess the differences make sense…
I noticed that the callback parameters on my local instance are a lot shorter than on the proxied instance. As this stuff is encoded (probably even encrypted), it is hard to spot specific details.
Local callback:
/rest/oauth2-credential/callback?code=M.C107_BL2.2.76072fed-68f9-b746-e1d0-2f9daf68720b&state=eyJ0b2tlbiI6Ik5UaGxwUERLLUFsSGwzWTFIRkQxaXFQTmlVbDAyZzJ5bGJFcyIsImNpZCI6IjQifQ%3d%3d
Remote callback:
/rest/oauth2-credential/callback?code=0.ATEAEnNYbTPEaE6VaN16NF6UzeGzLbzKEUFJrrT8r1SJeiAxAAA.AgABAAIAAAD--DLA3VO7QrddgJg7WevrAgDs_wUA9P9b9TmLmNBInjaF06n-e7Sspeol-y0QkJTbVIKLAVHhtHlECZyOORCJkf981DdBECwgN3zoyt6OJdoBqppzLjkvZRQfnAuhnQ2lZaP9ZziUFG35qOpgXQ0hgCQDIR0a6PISuF41MHWc9zVDkzlhmBx7R5oR47IIxxBl5J3GtOdm2u0je3GfwrkeYQ_-SyG_WkVBiecCUJHVVCuH8OFiKkjT8R-OEPfSr0B8HfsfJP4hiSgo-ToeadEZe0VK3mz0sx95nOqRK1TBd4VwMk5Wvg1qEQfgftdE23ttWK-MC5iEGZmGUxwYiGjhf2jUXMQY3xsqQNxoOjhHopHZGQ2piykA5PvSAwhpUXQmBJQxqG4JvOsz5P_LvwiLyXGJs6hxWfMs593Cqj6dPRT8W5vnq1JiwQm_K6hZHbSlY4mivLU1vW1N9A265RVLIch_m8CtbI5kFUz7wGMMpv1e7Mrmj2qGopC6c1EwCrdeQjZFiJrZvbVXNga7xKWIxKR_rkAt8yN9c8zp3lK4UmwyJbIIZMTTXDGD5CUSBoptQVqBU9WMz4BAPNbCaNMyeRoiRLEm8V7NjGovQ8NpUOm3ja7DseU0HoAyQXZ-XrVAUb5pb3N03pMaGXTDsKMsTRhh4COyarIvdHYYg9IEppOpUcVjXBxcx01lpLSAHlzsH9eIEepbR7M-58vg3YCgaf7MDnN8-yEgcc2BtcEYWe5g9AeghxcO2g7QGqzXkiAC5qet8AOLoO-rSDUYFxEQ0A07XmpBGPgzZHkrUbnqvCjSKDHB0s7joCmqiHspro3hXx_bCbYPO-FtZoLd4bY&state=eyJ0b2tlbiI6IkJkam5XbkViLXdtQ1VSUTFndlVFUDhWT2hBVFJ4ZGRmQk5LNCIsImNpZCI6IjYifQ%3d%3d&session_state=f8c1005b-22ef-4599-8f0c-337db7db927e
How important is the correct account type when setting up the application on the Microsoft account?