Hi All,
I am trying to experiment with self hosted n8n in kubernetes.
I am hosting my n8n version on my Mac using minikube.
- n8n version: 1.95.0 (deliberately used an old image so I can update it)
- Database (default: SQLite): postgres (self hosted as well in minikube
- n8n EXECUTIONS_PROCESS setting (default: own, main):
- Running n8n via (Docker, npm, n8n cloud, desktop app): kubernetes
- Operating system:
here the k8s deployment I am using (not I have anonymised sensitive field with <> but I have actual values there:
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
service: n8n
name: n8n
namespace: n8n-supabase-dev
spec:
replicas: 1
selector:
matchLabels:
service: n8n
strategy:
type: RollingUpdate #Recreate
rollingUpdate:
maxSurge: 1
maxUnavailable: 1
template:
metadata:
labels:
service: n8n
spec:
initContainers:
- name: volume-permissions
image: busybox:1.36
command: ["sh", "-c", "chown 1000:1000 /data"]
volumeMounts:
- name: n8n-claim0
mountPath: /data
containers:
- command:
- /bin/sh
args:
- -c
- sleep 5; n8n start
env:
- name: DB_TYPE
value: postgresdb
- name: DB_POSTGRESDB_HOST
value: postgres-service.n8n-supabase-dev.svc.cluster.local
- name: DB_POSTGRESDB_PORT
value: "5432"
- name: DB_POSTGRESDB_DATABASE
valueFrom:
secretKeyRef:
name: postgres-secret
key: POSTGRES_DB
- name: DB_POSTGRESDB_USER
valueFrom:
secretKeyRef:
name: postgres-secret
key: POSTGRES_NON_ROOT_USER
- name: DB_POSTGRESDB_PASSWORD
valueFrom:
secretKeyRef:
name: postgres-secret
key: POSTGRES_NON_ROOT_PASSWORD
- name: N8N_HOST
value: <<something>>
- name: N8N_PROTOCOL
value: http
- name: N8N_PORT
value: "5678"
- name: WEBHOOK_URL
value: <<webhook>>
- name: N8N_SMTP_HOST
value: <<something>>
- name: N8N_SMTP_PORT
value: "465"
- name: N8N_SMTP_USER
value: "apikey"
- name: N8N_SMTP_PASS
value: <<something>>
- name: N8N_SMTP_SENDER
value: <<something>>
- name: N8N_SECURE_COOKIE
value: "true"
# valueFrom:
# secretKeyRef:
# name: n8n-secret
# key: N8N_SECURE_COOKIE
# image: n8nio/n8n
image: n8nio/n8n:1.95.0
imagePullPolicy: Always
name: n8n
ports:
- containerPort: 5678
resources:
requests:
memory: "250Mi"
limits:
memory: "500Mi"
restartPolicy: Always
volumes:
- name: n8n-claim0
persistentVolumeClaim:
claimName: n8n-claim0
- name: n8n-secret
secret:
secretName: n8n-secret
- name: postgres-secret
secret:
secretName: postgres-secret
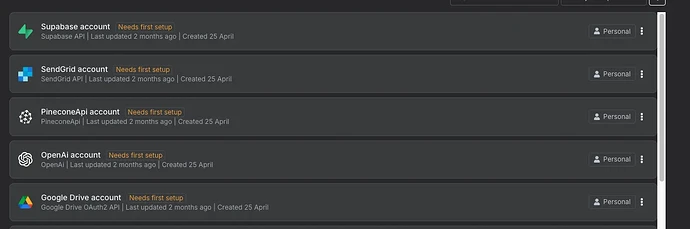
Basically when I update the image of the n8n container, all the stored credentials have “Need first setup”, so they are all empty.
Is there any setting I am missing?
Thanks for any reply