Problem Description
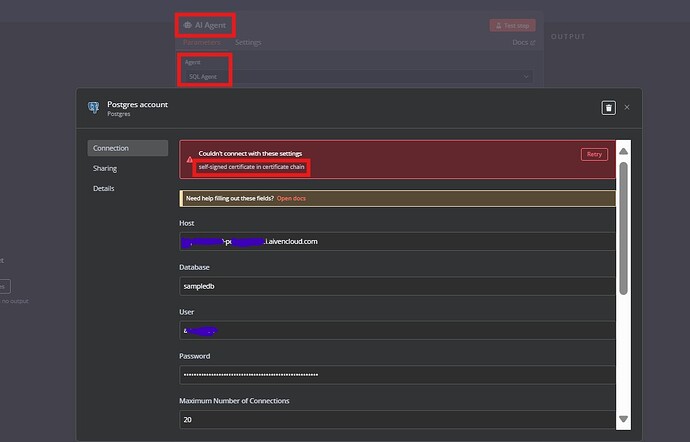
I am trying to connect my online PostgreSQL database (hosted on Avien.com) to n8n Cloud (version 1.80.5) using the SQL Agent node. The PostgreSQL database has SSL mode set to “require”, enforcing encrypted connections. However, when attempting to configure the connection in n8n, I encounter the following error:
Error Message:
self signed certificate in certificate chain
This error indicates that the PostgreSQL server is using a self-signed certificate (or a certificate signed by a custom CA), and n8n does not trust it by default.
Missing CA Certificate Configuration
While troubleshooting, I discovered that n8n’s PostgreSQL credentials form does not include an option to provide a CA certificate (CA token), which would allow n8n to properly verify the database’s SSL certificate. The PostgreSQL server on Avien.com generated a CA certificate, which I have, but I currently have no way to supply it to n8n via the standard credential form.
This lack of a CA certificate input is blocking the ability to establish a secure connection to the database.
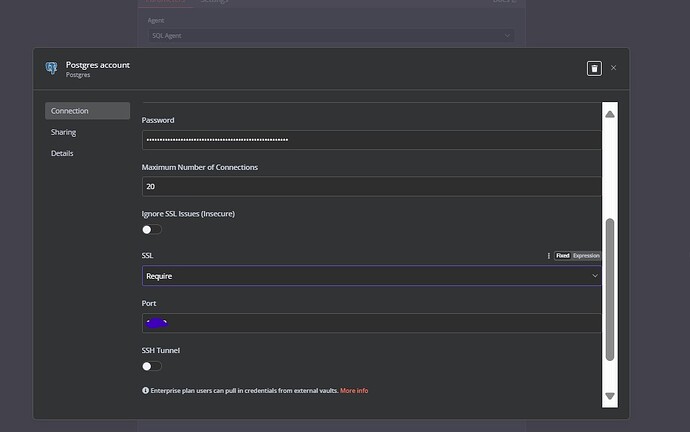
Ineffectiveness of “Ignore SSL Issues”
I also attempted to enable the “Ignore SSL Issues” option in the PostgreSQL credentials setup.
- While this does allow the initial connection to succeed, it does not resolve the issue during actual execution.
- At runtime, when the SQL Agent node is used in combination with an LLM (such as OpenAI, Claude, etc.), the error resurfaces and the workflow fails with the same
self signed certificate in certificate chainerror.
This confirms that ignoring SSL during setup does not fully bypass the problem, particularly in real-world agent executions.
Summary
- Platform: n8n Cloud (version 1.80.5)
- Node: SQL Agent
- Database: PostgreSQL (hosted on Avien.com, SSL mode = “require”)
- Error:
self signed certificate in certificate chain - Blocking Issue: n8n does not provide a way to upload or reference a CA certificate for PostgreSQL connections.
- Workaround Fails: The “Ignore SSL Issues” setting does not resolve the error during runtime execution with LLM integrations, particularly when the SQL Agent interacts with OpenAI, Claude, or similar models.
Desired Outcome
I am looking for official guidance or a supported method to properly configure SSL with a custom CA certificate in n8n Cloud, specifically when using the SQL Agent node to connect to a PostgreSQL database with SSL enabled.
If this is not currently possible, I would appreciate any recommended workarounds—or confirmation if this is a missing feature that needs to be logged.