TLDR
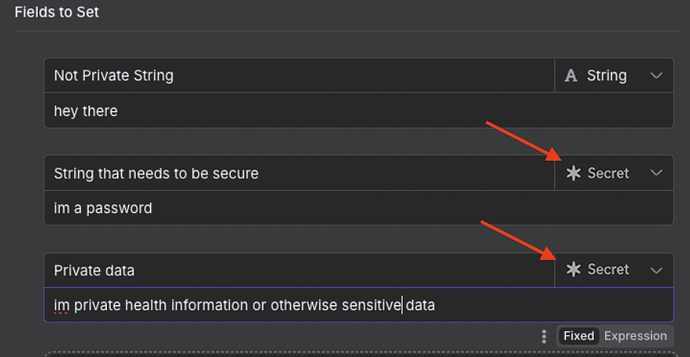
Lets make it possible to have private data and secrets in workflows by processing then redacting it before saving the execution history. Instead of string, use secret. It could look like this:
After the execution then that data is not saved to the db, similar to how built in auth handles it when you look at the logs.
Thoughts
I use a lot of custom auth implimentations, mostly JWT, that right now, HAS to be saved in plain text if you want to keep your execution history.
I also work with private/sensitive data, which either means i am avoiding n8n for that or making the tradeoffs of turning off execution data and being really really careful.
Right now in production, i often need to turn off execution history because of this, which makes troubleshooting errors a nightmare.
Implimentation
1. New Data Type
n8n adds a new type. So everywhere you work with fields, we’ll be able to specify secret instead of string. Secret would be the exact same thing as a string during execution, but then just wouldn’t save it and instead add a placeholder like jwt='*****'
2. Input Data from Webhooks/HTTP
There could be a field where we specify secret input. So then in the field we could just specify:
headers.authorization, body.name, body.dob, body.ssn
This mirrors how it already works in mutliple other nodes.
Then if the fields exist, they will be saved under the type secret.
Example
With this workflow, i pinned the data to give an example
How execution history looks now
![]() Click into the trigger and jwt and you can read the secret auth key
Click into the trigger and jwt and you can read the secret auth key
What I Want the Execution History to Look Like
![]() Click into the trigger and jwt to see it masked
Click into the trigger and jwt to see it masked
(note: this is pinned data that im showing as an example for execution history. I dont see a way that pinned data could be private)
Are you willing to work on this?
Sure.
In the chance this is implimented, i would really really hope it isn’t paywalled