The idea is:
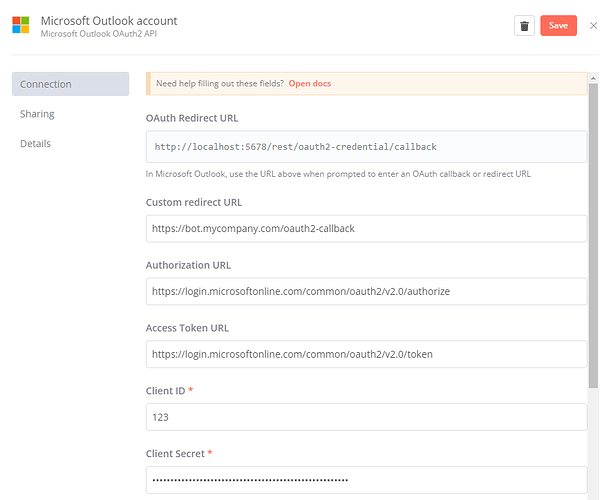
Let users set a custom redirect URL in OAuth 2 credentials.
My use case:
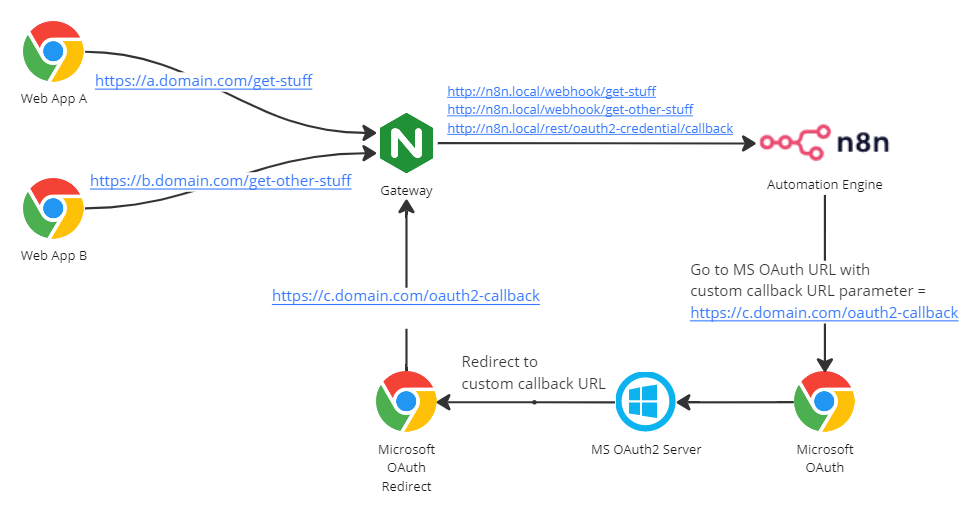
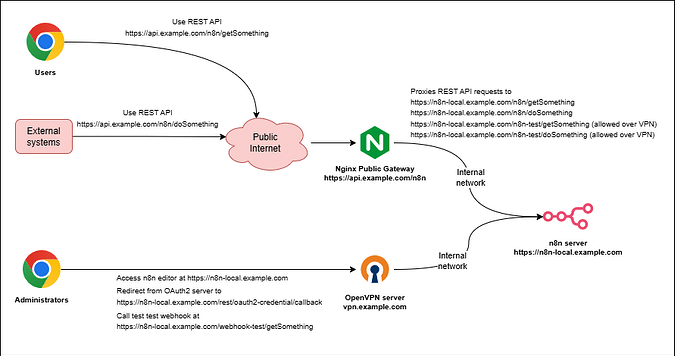
N8N is located in the internal network and unavailable from the outside.
I use NGinx public gateway and map private N8N webhooks to custom public URLs.
For example, I want to map private http://localhost:5678/rest/oauth2-credential/callback to public https://mydomain.com/oauth2-callback
I think it would be beneficial to add this because:
- Improve the security of N8N instances: the ability to hide the whole N8N and show publicly only specific endpoints.
- Use a single private N8N instance with multiple public subdomains.
- Create beautiful structured APIs.
- Use N8N behind an API Gateway.
Any resources to support this?
Are you willing to work on this?
I’ve already implemented this in my custom N8N build and am ready to send a PR if you don’t mind.
packages/nodes-base/credentials/OAuth2Api.credentials.ts
{
displayName: 'Custom redirect URL',
name: 'customRedirectUrl',
type: 'string',
default: '',
},
packages/cli/src/credentials/oauth2Credential.api.ts
const oAuthOptions: ClientOAuth2.Options = {
clientId: get(oauthCredentials, 'clientId') as string,
clientSecret: get(oauthCredentials, 'clientSecret', '') as string,
accessTokenUri: get(oauthCredentials, 'accessTokenUrl', '') as string,
authorizationUri: get(oauthCredentials, 'authUrl', '') as string,
redirectUri: get(
oauthCredentials,
'customRedirectUrl',
`${getInstanceBaseUrl()}/${restEndpoint}/oauth2-credential/callback`,
) as string,
scopes: split(get(oauthCredentials, 'scope', 'openid,') as string, ','),
state: stateEncodedStr,
};